We are beyond thrilled to share that Coliance has been...
Read MoreZero Trust security is a trending cybersecurity buzzword in the world right now with organisations scrambling to proactively secure their organisations. With EU legislators unifying data protection policies and laws throughout the EU and enforcing GDPR regulations with heavy penalties, it is not a concern to be taken lightly. This year alone, the ICO issued a fine of £22,046,000 to British Airways and one to Marriott International for £20,450,000 for hacked websites and cyberattacks that exposed the personal data of their customers and guests.
The question on everybody’s mind right now is how they can avoid these common data security pitfalls, especially if they operate with hybrid multi-cloud environments. The answer lies in the adaptation of Zero Trust policies, which is a monumental departure from the tradition of Trust by Verification. While the Zero Trust adoption process is complex and not a standalone, one-size-fits-all solution for your cybersecurity woes, we can still confidently assert:
Zero Trust is the new standard for cybersecurity that can protect you against the growing frequency and sophistication of cyberattacks and the resulting monetary loss.
The 2022 IBM Cost of data breach report results provide an excellent view of how dozens of factors impact the costs that keep adding up after a data breach occurs and some of the highlighted consequences are staggering:
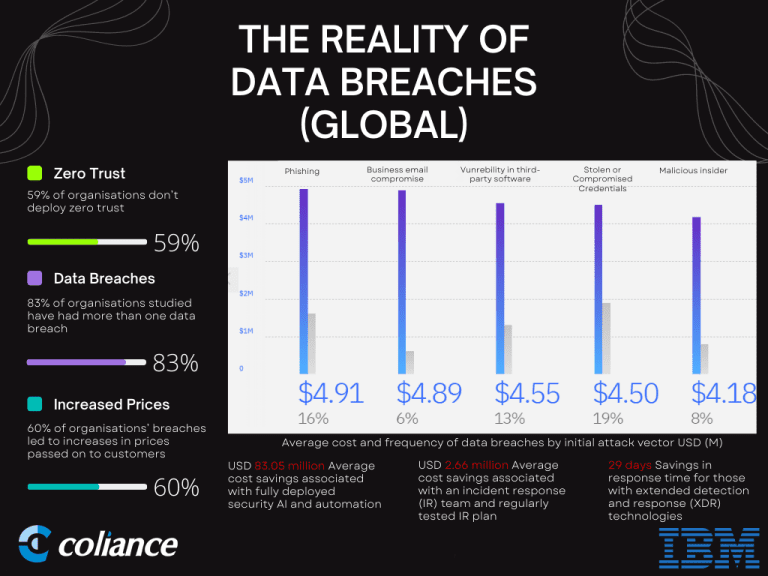
The UK was no stranger to cyberattacks in 2022 with several sectors impacted in the government and public sector. NHS111 was subject to a ransomware attack in August 2022 which knocked out several of their products, including Adastra which is used by 85% of NHS111 services to log calls and give over the phone medical advice. NHS111 call handlers had to resort to pen and paper for 3 weeks while the system was brought back online. South Staffordshire Water suffered a ransomware attack in August, followed by a major UK transport company in September who suffered scheduling issues with their bus drivers and services. Even the tourism industry was affected in 2022 when the Inter-Continental Hotel Group suffered data breaches and ransomware attacks. Cybercriminals can be very resourceful and sadly can be backed by nation-states. They often leverage sophisticated tools, such as Ransomware-as-a-Service, and can be incentivized by cryptocurrencies with their strong liquidity and poor traceability.
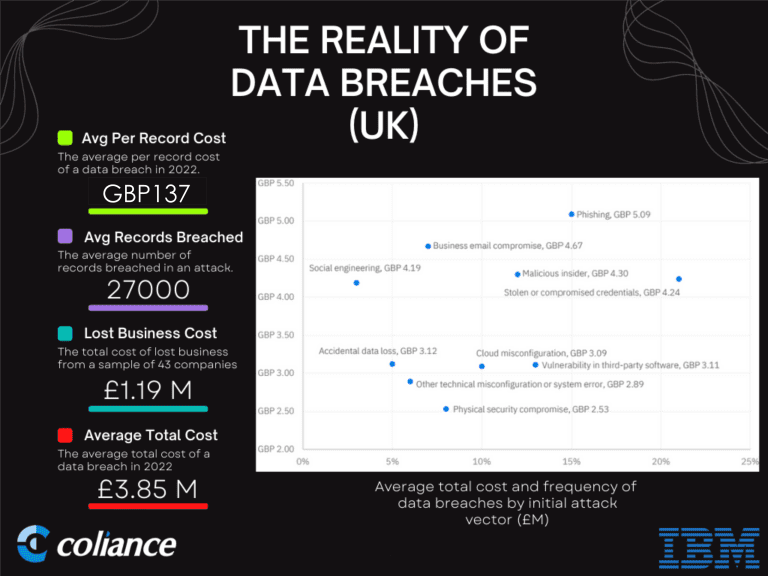
If you are rightly concerned and want to make changes to your own IT infrastructure, it’s important to understand that:
Implementing Zero Trust in your systems is not an application or a specific feature but an overall strategy that comprises a large variety of safety measures.
The core tenet of the Zero Trust security model is that all users, devices, and services should be considered a potential threat.
This far-reaching security management requirement makes most organisations worry about cost implications and the concern that changes may inevitably overwhelm their already complex network operations.
At Coliance we believe that implementing or expanding your Zero Trust strategy to help protect what is most valuable inside of your organization can start off small, with more protections added over time.
We have extensive experience and expertise in creating effective supply chain solutions for our clients and are confident we can help you combat growing cyber-attack and data breach threats. As an IBM Gold Business Partner, we leverage the value of IBM Sterling Zero Trust model solutions:
The Sterling Secure File Transfer (SFT) solution aligns with a Zero Trust approach and harden servers to help reduce the possibility for ransomware or malware to travel laterally. A Zero Trust approach requires securing and regulating movement between internal computers and servers as we remove untrusted protocols. SFT can also encrypt data at rest and in transit and provides multifactor authentication helping implement a Zero Trust strategy for your file transfers. Watch IBM Secure File Transfer (SFT) in action in this demo.
The established industry standard capabilities of MQ messaging, and the power of effective API integration management cloud solutions to deliver the secure, future-ready B2B solutions our clients need.
IBM Sterling File Gateway helps with dynamic routing, limiting any malware from spreading to other servers by only allowing listed servers to talk to authorized systems. IBM Sterling File Gateway encrypts data at rest, and in motion, minimizing effects if data loss occurs. It limits potential entry points into your network while still supporting common open-source protocols like FTP(S), SFTP, SSH, SCP, and HTTP(S) that are needed to power your business.
The IBM Sterling Connect: Direct allows list security architectures and has no reported breaches in its 30+ years of usage. It is a proprietary protocol with built in encryption that isn’t readily available to most bad actors, it utilizes a security-hardened protocol. When malware reaches out internally, it will not know how to ‘talk’ to the protocol. It can also check the IP address from the server that has requested access. If that IP address is not on the internal list of trusted servers, (which can be consistently updated), the receiving server automatically drops the session. It has additional checkpoints to further help prevent the spread of malware to another server. The malware will require the correct credentials, which can be increased for additional protection of high-value servers, and only files with a specified name may be transferred. Each server that uses Connect:Direct becomes a checkpoint – and choke point – for malware. This Zero Trust approach in Connect:Direct hardens infrastructure and includes capabilities for Zero Trust practices for communications that can help mitigate risks of traditional protocols using FTP, SFTP and SSH.
As an IBM Gold Business Partner, Coliance can help you can Authenticate and Authorize with Visibility and Governance.

It is time to recognize that your castle and moat security model is no longer relevant. Attackers can clear your barriers and will face no resistance as they move from device to device, infecting, stealing, and encrypting your data.
You can only avoid this if you have internal barriers and security checks in place that are provided by a Zero Trust model. While we reiterate that the Zero Trust adoption process is complex and not a standalone, one-size-fits-all solution, there is some good news:
Implementing Zero Trust security is flexible and can adjust to different situations to provide adequate protection against the latest threats and keep your data and digital infrastructure safe from harm.
Coliance can provide you with a solution that is tailored to the specific structure and needs of your organization. We can:
We will do all of this while your company enjoys continued access, service, and operations with a gradual transition to safety. Contact us today to implement a system that will bring both value and security to your organisation, improving both safety and your users experience.
We are beyond thrilled to share that Coliance has been...
Read MoreAchievement of Cyber Essentials Plus Certification Coliance Strengthens Cybersecurity Credentials...
Read MoreEmpowering Your Supply Chain: The Transformative Impact of Supply Chain...
Read MoreHow to Harness the Trend of the Decade – ESG...
Read MoreAgora – Striving towards supply chain resilience with B2B integration...
Read More3 steps to help protect your B2B transactions and file...
Read More
Coliance © 2024 All rights reserved