We are beyond thrilled to share that Coliance has been...
Read MoreIT jargon isn’t always easy to understand, but ‘ransomware’ is one term that should be self-explanatory.
Depriving someone of something or somebody they value to extort something from them has been around at least since the 12th Century, when the word ‘ransom’ was coined.
Ransomware is simply a piece of IT that deprives someone of access to another piece of IT with that same aim (security experts McAfee offer a more in-depth explanation here ).
The earliest recorded ransomware was the AIDS Trojan virus, launched in 1989. Like most ransomware, it introduced a computer program into the victim’s system that encrypted data and locked them out, then demanded money to reverse it. Fortunately, it used simple encryption, meaning it didn’t require access to information known only to the author to decrypt it, making it relatively straightforward to crack.
The AIDS Trojan ransomware attack used a virus to deliver its payload, like most ransomware. Although ransomware and viruses aren’t the same thing, it helps to think about ransomware in terms of how viruses work.
Just as the COVID virus infects hosts, spreads via these hosts and delivers its payload to affect the immune system, making many hosts ill, a ransomware virus infects, spreads and attacks through multiple hosts.
IT and our reliance on it has mushroomed in the thirty-two years since the AIDS Trojan.
Ransomware is an increasingly sophisticated and powerful type of Cybercrime. It has grown rapidly from its simple origins to become a tool of international organised crime, sometimes government sponsored.
The basic process remains the same – introduce a malicious file through email or any other inter-computer communication, encrypt data, lock users out, and demand a ransom.
Increasing sophistication makes ransomware ever harder to detect, and cybercriminals’ access to advanced cryptography techniques make decryption ever more complex.
Increasing reliance on critical systems, automation of industrial processes, growing supply chain complexity and developments like the Internet of Things (IoT) mean the disruptive power of ransomware has increased exponentially.
A successful ransomware attack on an automated water pumping station will stop water being supplied to homes. Attack a logistics company and goods deliveries will be delayed, disrupting the supply chain so that food processing units and supermarkets don’t receive raw or finished materials on time, leading to waste through spoilage and empty shelves. The knock-on effects can be massively costly.
An Internet search on ‘Ransomware growth’ returns multiple sources on the surge in ransomware in recent times, from one report citing a 93% increase in ransomware attacks in the first six months of 2021, to the head of the UK GCHQ citing a doubling of UK ransomware attacks in one year, to the widely publicised and damaging Colonial Pipeline attack and SolarWinds breach.
It’s estimated that a ransomware attack now happens somewhere in the world every 11 seconds, and the average direct ransomware payment in 2021 equates to around £414,000, up from £227,000 in 2020 and £132,000 in 2029. This is in addition to operational and reputational damage costs.
One impact of the COVID pandemic has been a massive increase in working from home, potentially heralding a permanent shift in working patterns. This shift creates new vulnerabilities for ransomware to exploit as more connections to corporate IT resources are made across insecure connections.
Top targets are financial and health services and, increasingly, manufacturing (up from 8th to 2nd most targeted sector in 2021) and logistics. Ransomware is a major threat to global supply chains already under stress from COVID, Brexit and other factors.
The impact is even more critical for health, financial services and other sectors that depend on 24/7 IT and face massive and increasing human and monetary impacts every moment systems remain down.
Recent ransomware growth is at least partly due to cybercriminals’ ability to defeat traditional moat-and-castle IT security architectures.
Historically, organisations have protected themselves against cyberattack by creating a protective ‘moat’ around their IT resources with firewalls and proxies.
Corporate IT resources still need to communicate externally, so authorised traffic is allowed through these defences via firewall rules and other measures constituting a virtual drawbridge.
Cybercriminals have learned ways to breach these defences and hide malware inside the organisation – a later blog will explore this.
A growing response to this threat is for organisations to adopt a zero-trust approach, one in which any interaction with or between systems, even one that appears to be entirely within the ‘castle’ is treated as untrusted as shown in the figure below.
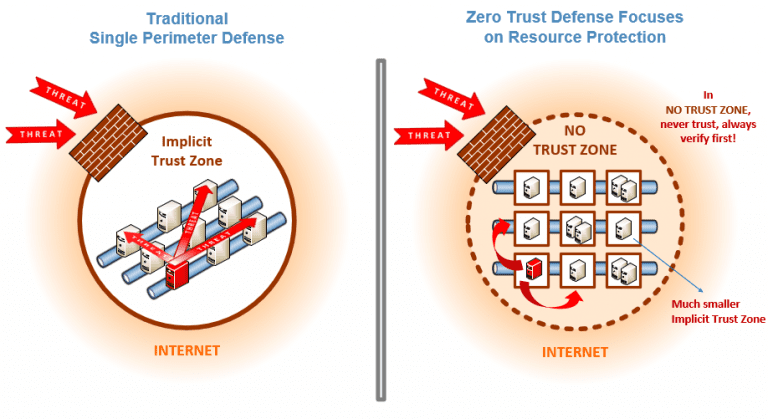
Source : NIST
At Coliance, we have extensive experience and expertise in creating effective supply chain solutions for our clients, and we can help you combat the growing ransomware threat.
As an IBM Gold Business Partner, we leverage the value of IBM Sterling solutions from secure file gateways to SFTP, the established industry standard capabilities of MQ messaging, and the power of effective API integration management cloud solutions to deliver the secure, future-ready B2B solutions our clients need.
To learn more about securing Supply Chain against ransomware and how Coliance can help, register for our e-Book here or contact us to continue the conversation at info@Coliance.co
We are beyond thrilled to share that Coliance has been...
Read MoreAchievement of Cyber Essentials Plus Certification Coliance Strengthens Cybersecurity Credentials...
Read MoreCybersecurity and Ransomware in the UK Today Cybersecurity is a...
Read MoreCastle-and-moat security – great for 11th Century castles, but it’s...
Read MoreWhy should I care about ransomware now? What is ransomware?...
Read More
Coliance © 2024 All rights reserved